Explain how they are used to provide network security.
Explain their advantages.
Provide diagrams on how each device is used with justifications.
1- Network Router
2- Network Access Control (NAC)
3- Wireless Intrusion Prevention and Detection System (WIDPS)
Answers:
1- Network Router - Description
- It is a device
- Forwards data packet along network
- It is connected at least two networks
- The two networks are commonly two LAN or two WAN, LAN and the ISP's network
- It is located at gateways. the place where two or more networks are connected.
- Only a small amount of filtering of data is done through routers.
Advantages
- Connect different network architectures, in example the Token Ring and Ethernet
- They can choose the best path across an internetwork using dynamic routing techniques
- By creating collision domains and broadcast domains, routers reduce network traffic
Explain how they are used to provide network security.
- Routers sit right at the gateway between your ISP’s network and your own, which makes them your first line of defense against a digital intruder — as long as they’re properly secured.
Provide diagrams on how each device is used.

Routers connect a modem — like a fiber, cable, or DSL modem — to other devices to allow communication between those devices and the internet. Most routers, even wireless routers, usually feature several network ports to connect numerous devices to the internet simultaneously.
Typically, a router connects physically, via a network cable, to the modem via the internet or WAN port and then physically, again via a network cable, to the network interface card in whatever wired network devices you may have. A wireless router can connect via various wireless standards to devices that also support the particular standard used.
The IP address assigned to the WAN or internet connection is a public IP address. The IP address assigned to the LAN or local network connection is a private IP address. The private IP addresses assigned to a router is usually the default gateway for the various devices on the network.
Wireless routers, and wired routers with multiple connections, also act as simple network switches allowing the devices to communicate with each other. For example, several computers connected to a router can be configured to share printers and files among themselves.
A router is a device that forwards data packets along networks. A router is connected to at least two networks, commonly two LANs or WANs or a LAN and its ISP's network. Routers are located at gateways, the places where two or more networks connect.
Routers use headers and forwarding tables to determine the best path for forwarding the packets, and they use protocols such as ICMP to communicate with each other and configure the best route between any two hosts.
Very little filtering of data is done through routers.
2- Network Access Control (NAC) - Description
- Network admission control
- A method of bolstering (strengthen) the security of proprietary network by do restriction of the availability of the network resources to endpoint devices that comply with a defined security policy
Advantages
- allows access to particular network
- allow the owner of the particular device to only do its job role
Explain how they are used to provide network security.
A NAC system can deny network access to noncompliant devices, place them in a quarantined area, or give them only restricted access to computing resources, thus keeping insecure nodes from infecting the network.
Provide diagrams on how each device is used.

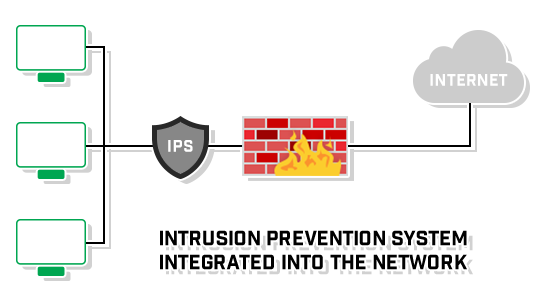
3- Wireless Intrusion Prevention and Detection System (WIPDS) - Description
- a standalone security device or integrated software application that monitors a wireless LAN network’s radio spectrum for rogue access points and other wireless security threats.
Explain how they are used to provide network security.
A WIDPS compares the list of MAC addresses of all connected wireless access points on a network against the list of authorized ones and alerts an IT staff when a mismatch is found. To avoid MAC address spoofing, some higher-end WIDPSes like Cisco ones are able to analyze the unique radio frequency signatures that wireless devices generate and block unknown radio fingerprints. When you find the rogue wireless mobile access point, you can suppress its signal by your access points. In addition to providing a layer of security for wireless LANS, WIDPSes are also useful for monitoring network performance and discovering access points with configuration errors. A WIDPS operates at the Data Link layer level of the OSI model.
Provide diagrams on how each device is used.
References
Cybrary. (2019). Advantages and Disadvantages of Routers - Cybrary. [online] Available at: https://www.cybrary.it/study-guides/ccna-exam-study-guide/advantages-and-disadvantages-of-routers/ [Accessed 16 Oct. 2019].
Taylored Systems | Indianapolis. (2017). Differences Between Routers & Firewalls in Network Security | Taylored. [online] Available at: https://www.taylored.com/blog/the-differences-between-routers-and-firewalls-in-network-security/ [Accessed 20 Oct. 2019].
Lifewire. (2019). What Is a Router (Residential Gateway) and How Does It Work?. [online] Available at: https://www.lifewire.com/what-is-a-router-2618162 [Accessed 20 Oct. 2019].


For any connection, the network plays a great role acting as an intermediary path between users. Best Cyber Security Solutions are considered for making the Network Security Devices so it does not get affected by attacks of malicious hackers.
ReplyDelete